- Research Article
- Open access
- Published:
An Efficient Watermarking Technique for the Protection of Fingerprint Images
EURASIP Journal on Information Security volume 2008, Article number: 918601 (2008)
Abstract
This paper describes an efficient watermarking technique for use to protect fingerprint images. The rationale is to embed the watermarks into the ridges area of the fingerprint images so that the technique is inherently robust, yields imperceptible watermarks, and resists well against cropping and/or segmentation attacks. The proposed technique improves the performance of optimum multibit watermark decoding, based on the maximum likelihood scheme and the statistical properties of the host data. The technique has been applied successfully on the well-known transform domains: discrete cosine transform (DCT) and discrete wavelet transform (DWT). The statistical properties of the coefficients from the two transforms are modeled by a generalized Gaussian model, widely adopted in the literature. The results obtained are very attractive and clearly show significant improvements when compared to the conventional technique, which operates on the whole image. Also, the results suggest that the segmentation (cropping) attack does not affect the performance of the proposed technique, which also provides more robustness against other common attacks.
1. Introduction
Biometric-based authentication systems that use physiological characteristics (fingerprint, face, iris, etc.) and/or behavioral traits (signature, voice, etc.) of persons are gaining more and more interest in the last years since they are based on information that is permanently associated with a person. Among various commercially available biometric-based systems, fingerprint-based techniques are the most mature, extensively studied, and widely deployed. While biometric-based techniques have inherent advantages over other authentication techniques such as token-based or knowledge-based techniques, ensuring the security and integrity of data is a paramount issue. Recently, watermarking techniques have been introduced and shown to be promising for protecting fingerprint data and increasing the security level of fingerprint-based systems [1–5]. For example, watermarking of fingerprint images can be used to secure central databases from which fingerprint images are transmitted on request to intelligence agencies in order to use them for identification and classification purposes (see Figure 1).
Depending on the embedding domain, existing algorithms for image watermarking usually operate either in the spatial domain [6, 7] or in a transform domain such as the discrete cosine transform (DCT) [8, 9] and the discrete wavelet transform (DWT) [10, 11]. However, most research works have been proposed in the transform domain because of its energy compaction property which suggests that the distortions introduced by the watermarks into the transform coefficients will spread over all the pixels in the spatial domain so as the changes introduced in these pixels values are visually less significant. Also, depending on the embedding rule used, the watermarks are often embedded using either an additive or a multiplicative rule. Additive rule has been broadly used in the literature due to its simplicity [8, 9, 12]. On the other hand, multiplicative rule is more efficient because it is image dependent and exploits the characteristics of the human visual system (HVS) in a better way [13–16].
Researchers in watermarking domain have focused their works on two fundamental issues: watermark detection and watermark decoding (extraction). In the latter, usually referred to as multibit watermarking, a full decoding is carried out to extract the hidden message, which can be an ownership identifiers, transaction dates, a serial numbers, and so forth. Such a watermarking can be found in fingerprinting, steganography, and the protection of intellectual property rights. In multibit watermarking, errors may occur when extracting the hidden message. Error probability can be used as a measure of the watermarking system performance.
In the literature, optimum decoders have been proposed and are based on a statistical modeling of the host data. Hernandez et al. propose a structure of optimum decoder for additive watermarks embedded within the DCT coefficients, modeled by a generalized Gaussian distribution (GGD). The problem of optimum decoding for multiplicative multibit watermarking has been addressed in [17–19]. In [17], the authors propose a new optimum decoder of watermarks embedded in the DFT coefficients modeled using a Weibull distribution, while Song in [18] proposes a general statistical procedure based on the total efficient score vector for both GGD and Weibull distribution. In [19], a new optimum decoder based on GGD has been proposed for extracting watermarks embedded within DWT coefficients.
In this work, the main contribution consists of embedding the watermark within the foreground or the ridges area by avoiding to embed it in the background area. This is motivated by the following facts.
-
(i)
Embedding watermarks into the ridges area increases its robustness because an attacker is interested in that area only (i.e., segmentation or cropping attack is usually performed to extract the ridges area from the background). Consequently, a part/portion of the watermark which is embedded within the background area can be removed, thus affecting the robustness of the watermark. Furthermore, to remove a watermark embedded in the ridges area, an attacker needs to apply strong attacks (such as additive noise and filtering) on that area, resulting in severe degradations of the quality of the image, thus, making it useless.
-
(ii)
The human eye is less sensitive to noise and changes in the texture regions; this makes sense to select the ridges area for watermark embedding and ensures imperceptibility of the embedded watermarks.
The proposed technique starts by first extracting the ridges area using the segmentation technique proposed by Wu et al. [20], which has been modified to generate adaptive thresholds instead of fixed ones. The output of the segmentation results in a binary mask called segmentation mask. This mask is then partitioned into nonoverlapping blocks, where only the blocks belonging to the ridges area are used to carry the watermark. This is represented by another binary mask called watermarking mask. The proposed technique has been introduced to increase the performance of the optimum watermark decoder, whose structure is theoretically based on a maximum-likelihood (ML) estimation scheme. For the sake of illustration, the process of watermarking is applied in both the DCT and the DWT domains, where the transform coefficients in each domain are statistically modeled using a GGD that has been shown, in the literature, to be the most accurate statistical model. The results obtained in this work clearly demonstrate the performance improvements achieved by the proposed technique. Also, the segmentation process, which can be thought of as an attack for fingerprint images, is shown to have no influence on the overall performance of the optimum decoder.
The paper is organized as follows. Section 2 describes the technique used to extract the region of interest. A brief description of watermark generation and the embedding process for both the DCT and the DWT domains is given in Section 3. Then, in Section 4, the multibit watermark decoding (extraction) issue is addressed. The influence of attacks on the overall performance of the optimum decoder is assessed through experimentation whose results and analysis are reported in Section 5. Finally, conclusions are drawn in Section 6.
2. Ridges Area Detection and Extraction
A captured fingerprint image usually consists of two areas: the foreground and the background. The foreground or ridges area is the component that originates from the contact of a fingertip with the sensor. The noisy area at the borders of the image is called the background area. An extraction of the ridges area can be carried out by using a segmentation technique whose objective is to decide whether a part of the fingerprint image belongs to the foreground (which is of our interest) or belongs to the background. Several methods and techniques have been proposed in the literature for segmenting fingerprint images [21, 22]. However, in our case, the technique must be robust to common watermarking attacks in the sense that it also detects the same ridges area even if a fingerprint image is subjected to attacks such as compression, filtering, noise addition. Unfortunately, most of these techniques are not robust enough to resist image manipulations. In this work, we propose to use Harris corner point features to segment the fingerprint images. A Harris corner detector is based on a local autocorrelation function of a signal to measure the local changes of the signal with patches shifted by a small amount in different directions [23]. It has been found in [20] that the strength of a Harris point in the foreground area is much higher than that in the background area. However, the authors proposed to use different thresholds, which are determined experimentally for each image. Also, they noticed that some noisy regions are likely to have a higher strength which cannot be eliminated even by using high threshold value and proposed to use a heuristic algorithm based on the corresponding Gabor response. In our case, we found that an adaptive threshold can be obtained by using Otsu thresholding method [24] which provides an excellent threshold for fingerprint images from different databases. When some morphological methods are applied to eliminate the noisy regions, excellent segmented images are obtained.
The output of the segmentation process yields a segmented image and/or a segmentation mask. Since Harris point features method is a pointwise method, the segmentation mask is a binary mask (i.e., 1 if the pixel is assigned to the foreground area and 0 otherwise) of the same size as the original image.
Once the ridges area is extracted, one has to ensure that the watermark will be embedded within this extracted area. We propose to divide the segmentation mask into nonoverlapping blocks, where each block is classified as ridge block or background block according to the number of foreground pixels belonging to the block at hand (in this paper, a block is considered to be a ridge block if and only if all the block's pixels are classified as a ridge pixel). Finally, a binary watermarking mask is produced with a value of 1 if the block belongs to the ridges area and 0 otherwise. Let  be a two-dimensional (2D) data representing the luminance component of the image with size
be a two-dimensional (2D) data representing the luminance component of the image with size  pixels and
pixels and  be 2D binary matrix representing the segmentation mask with
be 2D binary matrix representing the segmentation mask with  components.
components.  is partitioned into
is partitioned into  nonoverlapping blocks
nonoverlapping blocks  ,
,  , of
, of  pixels, where
pixels, where  and
and  . Let
. Let  , where
, where  and
and  be 2D binary sequence representing the watermarking mask. Then,
be 2D binary sequence representing the watermarking mask. Then,  is obtained as follows:
is obtained as follows:

To verify whether the segmentation technique extracts the ridges area accurately, we have assessed this technique using real fingerprint images from the FVC2004 databases (DB1, DB2, and DB3) [25]. The images properties for all selected databases are shown in Table 1. For the sake of illustration, only the results obtained on two fingerprint images (Figures 2, 3, and 4) from each database are reported because similar performances have been achieved while considering other images. The choice has been done on the basis of the variability of the ridges area size.
Since the watermarks are inserted in the  DCT blocks, the size of a block is chosen to be a multiple of 8. The experiments carried out have indicated that
DCT blocks, the size of a block is chosen to be a multiple of 8. The experiments carried out have indicated that  must be above 32 (
must be above 32 ( ) to provide the same mask even in the presence of attacks. Furthermore, extensive experiments were carried out to determine the limitations of each database in the presence of attacks such as wavelet scalar quantization (WSQ) compression [26], additive white Gaussian noise (AWGN), and mean filtering. These results are necessary since the computed watermarking mask (i.e., the selected blocks) will be used to carry the watermark. The first column of Table 2 reports the highest compression ratio (in bits per pixel) below which the technique was able to provide the same watermarking mask. The second column of Table 2 shows the results obtained for an AWGN attack. In the case of the mean filtering, the results are shown in the third column of Table 2. For each database, the mean peak signal-to-noise ratio (PSNR) values are also shown for each type of attack in order to assess the distortions introduced.
) to provide the same mask even in the presence of attacks. Furthermore, extensive experiments were carried out to determine the limitations of each database in the presence of attacks such as wavelet scalar quantization (WSQ) compression [26], additive white Gaussian noise (AWGN), and mean filtering. These results are necessary since the computed watermarking mask (i.e., the selected blocks) will be used to carry the watermark. The first column of Table 2 reports the highest compression ratio (in bits per pixel) below which the technique was able to provide the same watermarking mask. The second column of Table 2 shows the results obtained for an AWGN attack. In the case of the mean filtering, the results are shown in the third column of Table 2. For each database, the mean peak signal-to-noise ratio (PSNR) values are also shown for each type of attack in order to assess the distortions introduced.
As can be seen from Table 2, all test images that form the three databases are robust to mean filtering attack and the technique can extract the same watermarking mask even for a filtering attack with a window size of  . However, the test images from database DB2 are more sensitive to WSQ compression and AWGN attacks than the images from the other databases. Images from DB1 are very robust to WSQ compression and images from DB3 are less sensitive to AWGN.
. However, the test images from database DB2 are more sensitive to WSQ compression and AWGN attacks than the images from the other databases. Images from DB1 are very robust to WSQ compression and images from DB3 are less sensitive to AWGN.
3. Watermark Generation and Embedding
As mentioned previously, the DCT and DWT domains are used to embed the watermark. The DCT can be applied either to the entire image or blocks as in the JPEG standard [27] as well as the DWT. The watermarking algorithm considered in this work relies on the embedding of a spread spectrum watermark, which spreads the spectrum of the hidden signal over many frequencies making it difficult to detect [28]. The embedding stage starts by decomposing the fingerprint image into blocks as described in the previous section (i.e., spatial blocks of  pixels) and only the ridges area blocks are selected to carry the watermark. Thus, using a watermarking mask
pixels) and only the ridges area blocks are selected to carry the watermark. Thus, using a watermarking mask  , if
, if  , then block
, then block  is selected; otherwise, it remains unchanged.
is selected; otherwise, it remains unchanged.
Assuming that the watermark carries a hidden message M with information that can be used, for instance, to identify the intended recipient of the protected image; this message is mapped by an encoder into a binary sequence  of
of  bits (by denoting
bits (by denoting  for bit
for bit  and
and  for bit 0).
for bit 0).
Let  be a pseudorandom sequence uniformly distributed in
be a pseudorandom sequence uniformly distributed in  , generated using a pseudorandom sequence generator (PRSG) initialized by a secret key
, generated using a pseudorandom sequence generator (PRSG) initialized by a secret key  . This pseudorandom sequence is the spreading sequence of the system. Every bit from the sequence
. This pseudorandom sequence is the spreading sequence of the system. Every bit from the sequence  is then multiplied by a set from the sequence
is then multiplied by a set from the sequence  in order to generate an amplitude-modulated watermark, consisting of the spread of the bits
in order to generate an amplitude-modulated watermark, consisting of the spread of the bits  .
.
3.1. DCT Domain
After selecting the blocks to be watermarked, a DCT transform is applied on blocks of  pixels, as in the JPEG algorithm [29]. Specifically, the application of the DCT on
pixels, as in the JPEG algorithm [29]. Specifically, the application of the DCT on  blocks leads to 64 coefficients which are zigzag scanned (i.e., arranged in decreasing order) to obtain one dimensional vector
blocks leads to 64 coefficients which are zigzag scanned (i.e., arranged in decreasing order) to obtain one dimensional vector  representing the entire set of the DCT coefficients to be watermarked (the DC component for each block is not used). In order to increase the security level, we propose to introduce some uncertainty about the selected coefficients altered by permuting the coefficients in
representing the entire set of the DCT coefficients to be watermarked (the DC component for each block is not used). In order to increase the security level, we propose to introduce some uncertainty about the selected coefficients altered by permuting the coefficients in  using a key
using a key  .
.
The information bits  are hidden as follows.
are hidden as follows.
-
(i)
The sequence
 is partitioned into
is partitioned into 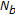 nonoverlapping sets
nonoverlapping sets  . In the following we denote by
. In the following we denote by 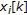 the coefficients belonging to the set
the coefficients belonging to the set 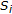 , where
, where  for
for  and
and  .
. -
(ii)
The watermark sequence
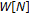 is divided into
is divided into  nonoverlapping chunks
nonoverlapping chunks 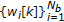 , where
, where 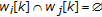 for
for 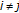 and
and 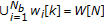 , so that each chunk
, so that each chunk  is associated to one block
is associated to one block 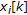 and both are used to carry one information bit
and both are used to carry one information bit 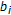 .
. -
(iii)
Each element of a chunk
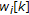 is multiplied by +1 or -1 according to its associated information bit
is multiplied by +1 or -1 according to its associated information bit  . The result of this multiplication is an amplitude-modulated watermark
. The result of this multiplication is an amplitude-modulated watermark 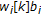 .
. -
(iv)
The watermark is embedded using a multiplicative rule as follows:
 (2)
(2)where
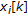 and
and 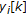 represent the set of the original coefficients and the associated watermarked coefficients belonging to the set
represent the set of the original coefficients and the associated watermarked coefficients belonging to the set 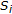 , respectively.
, respectively. 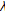 is a gain factor used to control the strength of the watermark by amplifying or attenuating the watermark effect on each DCT coefficient, so that the watermark energy is maximized while the alterations suffered by the image are kept invisible.
is a gain factor used to control the strength of the watermark by amplifying or attenuating the watermark effect on each DCT coefficient, so that the watermark energy is maximized while the alterations suffered by the image are kept invisible.
The hidden watermark can be retrieved if one knows (a) the entire procedure through which the watermark has been generated, (b) the secret key  used to initialize the PRSG, and (c) the second key
used to initialize the PRSG, and (c) the second key  which is used to permute the coefficients. Thus, an attacker will not be able to extract the watermark without knowledge of the secrete keys
which is used to permute the coefficients. Thus, an attacker will not be able to extract the watermark without knowledge of the secrete keys  and
and  , even if the entire watermark generation and embedding process are known.
, even if the entire watermark generation and embedding process are known.
3.2. DWT Domain
Each block selected to carry the watermark is transformed using the DWT at a level  , which produces (i) a low-resolution subband
, which produces (i) a low-resolution subband  , (ii) high-resolution horizontal subbands
, (ii) high-resolution horizontal subbands  , (iii) high-resolution vertical subbands
, (iii) high-resolution vertical subbands  and (iv) high-resolution diagonal subbands
and (iv) high-resolution diagonal subbands  . A watermark should be embedded in the high-resolution subbands, where the human eye is less sensitive to noise and distortions [30, 31]. In this work, all coefficients of the high-resolution subbands are used to carry the watermark sequence and the set of coefficients to watermarked
. A watermark should be embedded in the high-resolution subbands, where the human eye is less sensitive to noise and distortions [30, 31]. In this work, all coefficients of the high-resolution subbands are used to carry the watermark sequence and the set of coefficients to watermarked  is defined as
is defined as  . The watermark is then embedded by following the same steps described above for the DCT domain.
. The watermark is then embedded by following the same steps described above for the DCT domain.
4. Optimum Watermarking Decoder
In the watermark decoding process, the decoder obtains an estimate  of the hidden message
of the hidden message  embedded in the watermarked coefficients
embedded in the watermarked coefficients  . By assuming that all possible messages
. By assuming that all possible messages  are equiprobable, a maximum-likelihood (ML) criterion can be used to minimize the error probability and hence derive a structure for an optimum decoder. An optimum ML decoder would decide
are equiprobable, a maximum-likelihood (ML) criterion can be used to minimize the error probability and hence derive a structure for an optimum decoder. An optimum ML decoder would decide  , such that
, such that

where  is the PDF of the set
is the PDF of the set  conditioned to the events
conditioned to the events  and
and  . By assuming that (i) the coefficients
. By assuming that (i) the coefficients  are statistically independent, this assumption is justified for the DCT coefficients given the uncorrelated properties of the DCT for common images and also justified for the DWT coefficients, and (ii) the hidden sequence
are statistically independent, this assumption is justified for the DCT coefficients given the uncorrelated properties of the DCT for common images and also justified for the DWT coefficients, and (ii) the hidden sequence  and the values in
and the values in  are independent of each other, (3) can be written as
are independent of each other, (3) can be written as

where  indicates the coefficients of the set
indicates the coefficients of the set  carrying the bit
carrying the bit  , and
, and  is a set from
is a set from  associated to the same bit
associated to the same bit  . The decision criterion for the bit
. The decision criterion for the bit  can be expressed as
can be expressed as

According to the multiplicative rule used to embed the watermark, the PDF  of a marked coefficient
of a marked coefficient  subject to a watermark value
subject to a watermark value  and
and  can be expressed as
can be expressed as

where  indicates the PDF of the original, nonwatermarked coefficients. Substituting (6) in (5), the estimate bit
indicates the PDF of the original, nonwatermarked coefficients. Substituting (6) in (5), the estimate bit  is given by [19]
is given by [19]

The host coefficients of the DCT and the DWT can be modeled by the Laplacian model [32, 33]. However, they are widely modeled using a zero-mean GGD whose PDF is given by

where  is a Gamma function,
is a Gamma function,  ,
,  . The parameter
. The parameter  is referred to as the scale parameter representing the width of the PDF peak (standard deviation) and
is referred to as the scale parameter representing the width of the PDF peak (standard deviation) and  is called the shape parameter which is inversely proportional to the decreasing rate of the peak. Note that
is called the shape parameter which is inversely proportional to the decreasing rate of the peak. Note that  and
and  yield Laplacian and Gaussian distributions, respectively. The parameters
yield Laplacian and Gaussian distributions, respectively. The parameters  and
and  can be estimated as described in [34]. Practically,
can be estimated as described in [34]. Practically,  can be estimated by solving the following equations of [34]
can be estimated by solving the following equations of [34]

where  and
and  are the estimates of the mean absolute value and the variance of the sample dataset, respectively.
are the estimates of the mean absolute value and the variance of the sample dataset, respectively.  is the length of the dataset
is the length of the dataset  . The function F is defined as
. The function F is defined as

In practical situations, the solution of (9) can be found quickly by using an interpolation and a look-up table. Once the value of  is estimated,
is estimated,  is computed using the following expression:
is computed using the following expression:

Substituting (8) in (7), one obtains

5. Experimental Results
To gauge the effectiveness of our proposed technique, experiments were performed with test images from the databases FVC2004 (DB1, DB2, and DB3). In the DWT domain, the images were transformed using Daubechies9/7 wavelets [35] at the 3rd decomposition level and all coefficients of the high-resolution subbands ( ,
,  , and
, and  subbands of the levels
subbands of the levels  ) were used to carry the watermark. Daubechies9/7 wavelets were used because they have been adopted by the FBI as part of the WSQ compression standard for fingerprint images [36]. In all experiments, a blind watermark decoding is used so that the parameters
) were used to carry the watermark. Daubechies9/7 wavelets were used because they have been adopted by the FBI as part of the WSQ compression standard for fingerprint images [36]. In all experiments, a blind watermark decoding is used so that the parameters  and
and  of each set
of each set  are directly estimated from the DCT and the DWT coefficients of the watermarked images since the strength
are directly estimated from the DCT and the DWT coefficients of the watermarked images since the strength  is chosen to be sufficiently small to not alter the visual quality of the original images. For the sake of fair comparison, the performance of the proposed technique is compared against the conventional technique using the same decoder. By conventional watermarking, it is meant a technique which operates on the whole transform coefficients as described in [10, 19]. The performance is assessed by the bit error rate (BER), that is, the average number bit errors. For the sake of illustration, only results related the test images shown in Figures 2, 3, and 4 are plotted because the results from other images are very similar.
is chosen to be sufficiently small to not alter the visual quality of the original images. For the sake of fair comparison, the performance of the proposed technique is compared against the conventional technique using the same decoder. By conventional watermarking, it is meant a technique which operates on the whole transform coefficients as described in [10, 19]. The performance is assessed by the bit error rate (BER), that is, the average number bit errors. For the sake of illustration, only results related the test images shown in Figures 2, 3, and 4 are plotted because the results from other images are very similar.
As mentioned earlier, embedding the watermark in the ridges area (highly textured area) allows the use of a higher strength  than that used by the conventional technique at the same imperceptibility level measured by PSNR. This is illustrated by Table 3.
than that used by the conventional technique at the same imperceptibility level measured by PSNR. This is illustrated by Table 3.
 with
with  for both the proposed technique and the conventional technique.
for both the proposed technique and the conventional technique.It is worth noting that, in the proposed method, the number of bits that an image can carry is image dependent; more precisely it depends heavily on the size of the ridges area: the larger the ridges area is, the more bits can be hidden, and vice versa. Table 4 shows an example of the number of bits that test images can carry with the number of coefficients per set  As can be seen, images with large ridges area (image 98_2, image 71_4, and image 47_3) allow more bits to be hidden than images with relatively smaller ridges area (image 20_1, image 75_7, and image 73_7).
As can be seen, images with large ridges area (image 98_2, image 71_4, and image 47_3) allow more bits to be hidden than images with relatively smaller ridges area (image 20_1, image 75_7, and image 73_7).
In the first analysis, the BER as a function of the number of coefficients in the set  is investigated and assessed. This will help to (a) estimate the number of coefficients necessary for the extraction of the hidden message with low BER and (b) determine the number of bits that an image can hold. The results shown by Figures 5 and 6 were obtained by averaging out 100 watermark sequences randomly generated. The value of
is investigated and assessed. This will help to (a) estimate the number of coefficients necessary for the extraction of the hidden message with low BER and (b) determine the number of bits that an image can hold. The results shown by Figures 5 and 6 were obtained by averaging out 100 watermark sequences randomly generated. The value of  was set to obtain a PSNR value
was set to obtain a PSNR value  40 for all test images.
40 for all test images.
As can be seen from Figures 5 and 6, the proposed technique outperforms the conventional one, even without applying any attack. Another point that should be raised is the influence of the size of sets  on the performance of the decoder: the larger the set, the better the results. This is justified by the fact that a larger set provides more redundancy in the sense that each bit is carried by a higher number of coefficients. Furthermore, from the view point of implementation, a large set can be accurately modeled and the distribution of its coefficients is well approximated. However, in the case of the conventional technique operating on images from DB1 (i.e., image 98_2 and image 20_1, where the background is almost white), the BER is high and almost unchanged against an increase of the size of
on the performance of the decoder: the larger the set, the better the results. This is justified by the fact that a larger set provides more redundancy in the sense that each bit is carried by a higher number of coefficients. Furthermore, from the view point of implementation, a large set can be accurately modeled and the distribution of its coefficients is well approximated. However, in the case of the conventional technique operating on images from DB1 (i.e., image 98_2 and image 20_1, where the background is almost white), the BER is high and almost unchanged against an increase of the size of  . One can explain this by the fact that, in general, since a white background and smooth areas produce large number of null coefficients in both the DCT and DWT domains and according to the multiplicative rule used, these null coefficients cannot carry significant portion of watermark, thereby making these coefficients not reliable for decoding.
. One can explain this by the fact that, in general, since a white background and smooth areas produce large number of null coefficients in both the DCT and DWT domains and according to the multiplicative rule used, these null coefficients cannot carry significant portion of watermark, thereby making these coefficients not reliable for decoding.
We have also investigated the variations of BER against the total number of hidden information bits. The results are plotted in Figures 7 and 8 for the DCT and the DWT domains, respectively. As can be seen, for images form DB2 and DB3, the BER is lower for the proposed technique than that for the conventional one in the case of small number of bits. However, as the number of bits becomes higher, the conventional technique outperforms the proposed one. This is justified by the fact that the proposed technique provides coefficients with higher amplitudes, allowing the embedding of watermarks with higher amplitudes. Therefore, for small number of bits, the proposed technique can provide enough coefficients for each bit. On the other hand, the conventional technique has more coefficients than the proposed one. Consequently, for large number of bits, the set  is much larger than that of the proposed technique, thus allowing for the decoding of the watermark with lower BERs. For images DB1, the proposed technique outperforms the conventional one for both the DCT and DWT domains.
is much larger than that of the proposed technique, thus allowing for the decoding of the watermark with lower BERs. For images DB1, the proposed technique outperforms the conventional one for both the DCT and DWT domains.
As mentioned previously, a common attack that one can apply to fingerprint images is the segmentation because this technique preserves most of the ridges area and removes the background (i.e., removes the watermark embedded within the background while keeping the ridges area unaltered). First, we have investigated the dispersion of the watermarks in the spatial domain in the case of the conventional technique before showing the portions/parts of the image removed by the segmentation process (i.e., the portion of the watermark removed by the segmentation). Figures 9, 10, and 11(a:1, b:1) show the difference images between the original images and the corresponding watermarked images while Figures 9, 10, and 11(a:2, b:2) represent this difference image without the watermarked ridges area, which corresponds to the removed watermark. Here, we only display the results related to the DCT domain as the results obtained from embedding in the DWT domain are very similar. As can be seen, a relatively large part of the watermark is embedded within the background area, especially images with small ridges area (i.e., image 75_7 and image 73_7), which can be easily removed by segmenting the image. In addition, it can be said that images from database DB1 make the exception so that most of the watermark is embedded within the ridges area and, thus, the segmentation process will not affect significantly the decoding performance and, as explained above, this is due to the fact that a white background produces null coefficients thereby ruling it out for any effective watermark embedding.
The next analysis consists of extending the previous experiments but on the segmented images. The results of the first experiment are plotted in Figures 12 and 13 for the DCT and DWT domains, respectively, while the results of the second experiment are plotted in Figures 14 and 15 for the DCT and the DWT domains, respectively. In the case of our proposed technique, it can be seen from the figures that the BER is similar to that of the first experiment, thereby, confirming that the segmentation process has no influence on the performance of the decoding process and the watermark remains unaltered. For the conventional technique, the BER increases significantly and the segmentation process causes a considerable loss of the watermark information for images from databases DB2 and DB3. However, as expected, the BER is unchanged in the case of images from DB1.
Extensive experiments have also been conducted to gauge the performance of the proposed technique with respect to robustness in comparison with the conventional technique. Three sets of experiments have been carried out to measure the robustness of the watermark against the common attacks, namely, WSQ compression, mean filtering, and AWGN. In all these experiments, the value of the strength  is chosen in such a way to obtain PSNR value
is chosen in such a way to obtain PSNR value  40 and the number of coefficients per bit is set to 500. Each attack has been applied several times by varying the attack strength and reporting the average value of BER over 100 different pseudorandom watermarks. Note that results related to one image from each database are plotted since results of other images are similar.
40 and the number of coefficients per bit is set to 500. Each attack has been applied several times by varying the attack strength and reporting the average value of BER over 100 different pseudorandom watermarks. Note that results related to one image from each database are plotted since results of other images are similar.
Robustness against WSQ compression is assessed by iteratively applying the WSQ compression on the watermarked images using the WSQ viewer [37] varying the bit-rate value measured by bits per pixel (bpp). The results for the embedded watermark in the DCT and DWT domains are illustrated by Figure 16. Due to the segmentation technique used to extract the ridges area (see Section 2), the compression ratio is varied between 1.5 bpp and 0.5 bpp for images from DB1 and DB2, and between 1 bpp and 2 bpp for images from DB3. It is worth mentioning that for all images and the two domains, the WSQ compression does not affect significantly the ridges; the visual alterations are more severe in the background especially around the ridges area. This is due to the fact that the human eye is less sensitive to changes in textured areas. As can be seen from Figure 16, the proposed technique outperforms the conventional technique for all compression ratios.
Figure 17 shows the results for BER of watermarked fingerprint images corrupted by AWGN in the DCT and the DWT domains. The Gaussian noise is added with different value of signal-to-noise ratio (SNR). For all images and both domains, our proposed technique provides attractive results and significantly outperforms the conventional technique. The results for degradations due to a linear mean filtering are presented in Figure 18. The watermarked fingerprint images are blurred using mean filter with different sizes. It is worth noting that mean filtering causes a significant degradation to the visual quality of the images even for window size of  . In addition, this process affects severely the embedded watermark and the decoder produces high error rates. For both transform domains, the proposed technique performs significantly better than the conventional one for images from DB1 (improvement of 0.25 for filter window size
. In addition, this process affects severely the embedded watermark and the decoder produces high error rates. For both transform domains, the proposed technique performs significantly better than the conventional one for images from DB1 (improvement of 0.25 for filter window size  ) while the differences are very marginal for databases DB2 and DB3 (around 0.01 in terms of BER).
) while the differences are very marginal for databases DB2 and DB3 (around 0.01 in terms of BER).
6. Conclusions
This paper proposes an efficient technique for use in fingerprint images watermarking. The rationale of the technique consists of embedding the watermark into the ridges area of the fingerprint images which constitutes the region of interest. The key features of the proposed technique are to (i) preserve the watermark from segmentation which can be considered as a special case of the cropping attack, (ii) increase the robustness of the watermark against known attacks such as filtering, noise, and compression, and (iii) allow to embed imperceptible watermarks by embedding in highly textured areas. The technique starts by first extracting the ridges area from fingerprint images using the segmentation technique proposed by Wu et al. [20], which has been modified to generate adaptive thresholds instead of fixed ones, thereby making it more practical. This leads to a binary mask referred to as the segmentation mask. In order to ensure that the full watermark is embedded into the ridges area, the segmentation mask is partitioned into blocks, represented by another binary mark called watermarking mask.
The proposed technique has been applied to the optimum multibit, multiplicative watermark decoding. The watermark is embedded in the well-known transform domains, namely, the DCT and the DWT. The optimum decoder is based on the ML scheme and the coefficients of the two domains are modeled by a generalized Gaussian distribution. It is worth mentioning that the number of bits that an image can carry is image dependent (i.e., it depends on the ridges area meaning that a larger area allows more bits to be embedded and vice versa). The results obtained clearly show the improvements introduced by the proposed technique even in the absence of attacks. Furthermore, as the segmentation technique removes the part of the watermark embedded within the background area, it affects the performance of the conventional optimum decoder. However, this attack has no effect on the proposed technique. Moreover, the proposed technique provides more robustness in the presence of attacks such as WSQ compression, mean filtering, and additive white noise.
Finally, it should be mentioned that the proposed technique can be easily applied to other biometric images such as face, hand, and iris, since this type of images has only one defined region of interest. Also, it can be used to some natural images whose region of interest can be defined and extracted.
References
Jain AK, Uludag U: Hiding biometric data. IEEE Transactions on Pattern Analysis and Machine Intelligence 2003,25(11):1494-1498. 10.1109/TPAMI.2003.1240122
Ratha NK, Connell JH, Bolle RM: Secure data hiding in wavelet compressed fingerprint images. Proceedings of the ACM Workshops on Multimedia Conference, October-November 2000, Los Angeles, Calif, USA 127-130.
Gunsel B, Uludag U, Tekalp AM: Robust watermarking of fingerprint images. Pattern Recognition 2002,35(12):2739-2747. 10.1016/S0031-3203(01)00250-3
Zebbiche K, Ghouti L, Khelifi F, Bouridane A: Protecting fingerprint data using watermarking. Proceedings of the 1st NASA/ESA Conference on Adaptive Hardware and Systems (AHS '06), June 2006, Istanbul, Turkey 451-456.
Zebbiche K, Khelifi F, Bouridane A: Optimum detection of multiplicative-multibit watermarking for fingerprint images. Proceedings of the 2nd International Conference on Advances in Biometrics (ICB '07), August 2007, Seoul, Korea, Lecture Notes in Computer Science 4642: 732-741.
Yoshida M, Fujita T, Fujiwara T: A new optimum detection scheme for additive watermarks embedded in spatial domain. Proceedings of International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP '06), December 2006, Pasadena, Calif, USA 101-104.
Karybali IG, Berberidis K: Efficient spatial image watermarking via new perceptual masking and blind detection schemes. IEEE Transactions on Information Forensics and Security 2006,1(2):256-274. 10.1109/TIFS.2006.873652
Hernandez JR, Amado M, Perez-Gonzalez F: DCT-domain watermarking techniques for still images: detectorperformance analysis and a new structure. IEEE Transactions on Image Processing 2000,9(1):55-68. 10.1109/83.817598
Briassouli A, Strintzis MG: Locally optimum nonlinearities for DCT watermark detection. IEEE Transactions on Image Processing 2004,13(12):1604-1617. 10.1109/TIP.2004.837516
Ng TM, Garg HK: Wavelet domain watermarking using maximum-likelihood detection. Security, Steganography, and Watermarking of Multimedia Contents VI, January 2004, San Jose, Calif, USA, Proceedings of SPIE 5306: 816-826.
Khelifi F, Bouridane A, Kurugollu F, Thompson AI: An improved wavelet-based image watermarking technique. Proceedings of IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS '05), September 2005, Como, Italy 588-592.
Cheng Q, Huang TS: An additive approach to transform-domain information hiding and optimum detection structure. IEEE Transactions on Multimedia 2001,3(3):273-284. 10.1109/6046.944472
Barni M, Bartolini F, De Rosa A, Piva A: A new decoder for the optimum recovery of nonadditive watermarks. IEEE Transactions on Image Processing 2001,10(5):755-766. 10.1109/83.918568
Cheng Q, Huang TS: Robust optimum detection of transform domain multiplicative watermarks. IEEE Transactions on Signal Processing 2003,51(4):906-924. 10.1109/TSP.2003.809374
Khelifi F, Bouridane A, Kurugollu F: On the optimum multiplicative watermark detection in the transform domain. Proceedings of IEEE International Conference on Image Processing (ICIP '06), October 2006, Atlanta, Ga, USA 1373-1376.
Huang X, Zhang B: Statistically robust detection of multiplicative spread-spectrum watermarks. IEEE Transactions on Information Forensics and Security 2007,2(1):1-13.
Barni M, Bartolini F, De Rosa A, Piva A: Optimum decoding and detection of multiplicative watermarks. IEEE Transactions on Signal Processing 2003,51(4):1118-1123. 10.1109/TSP.2003.809371
Song K-S: Blind efficient scores detection and decoding of multibit watermarks. Mathematics of Data/Image Coding, Compression, and Encryption VIII, with Applications, August 2005, San Diego, Calif, USA, Proceedings of SPIE 5915: 1-10.
Zebbiche K, Khelifi F, Bouridane A: Multibit decoding of multiplicative watermarking for fingerprint images. Proceedings of the 4th IET International Conference on Visual Information Engineering (VIE '07), July 2007, London, UK 1095-1103.
Wu C, Tulyakov S, Govindaraju V: Robust point-based feature fingerprint segmentation algorithm. Proceedings of the 2nd International Conference on Biometrics (ICB '07), August 2007, Seoul, Korea, Lecture Notes in Computer Science 4642: 1095-1103.
Chen X, Tian J, Cheng J, Yang X: Segmentation of fingerprint images using linear classifier. EURASIP Journal on Applied Signal Processing 2004,2004(4):480-494. 10.1155/S1110865704309194
Alonso-Fernandez F, Fierrez-Aguilar J, Ortega-Garcia J: An enhanced gabor filter-based segmentation algorithm for fingerprint recognition systems. Proceedings of the 4th International Symposium on Image and Signal Processing and Analysis (ISPA '05), Septembre 2005, Zagreb, Croatia 15: 239-244.
Harris C, Stephens M: A combined corner and edge detector. Proceedings of the 4th Alvey Vision Conference, September 1988, Manchester, UK 15: 147-151.
Otsu N: A threshold selection method from gray-level histograms. IEEE Transactions on Systems, Man and Cybernetics 1979,9(1):62-66.
Fingerprint verification competition http://biometrics.cse.msu.edu/fvc04db/index.html
U.S. Federal Bureau of Invetigation : WSQ gray-scale fingerprint image comprssion specification. February 1993
Nelson M: The Data Compression Book. MT Press, New York, NY, USA; 1992.
Proakis JG: Digital Communications. McGraw Hill, New York, NY, USA; 2000.
Wallace GK: The JPEG still picture compression standard. IEEE Transactions on Consumer Electronics 1992,38(1):18-34.
Xia X-G, Boncelet CG, Arce GR: Wavelet transform based watermark for digital images. Optics Express 1998,3(12):497-511. 10.1364/OE.3.000497
Langelaar GC, Styawan I, Lagendijk RL: Watermarking digital image and video data: a state-of-the-art overview. IEEE Signal Processing Magazine 2000,17(5):20-46. 10.1109/79.879337
Simitopoulos D, Tsaftaris SA, Boulgouris NV, Briassouli A, Strintzis MG: Fast watermarking of MPEG-1/2 streams using compressed-domain perceptual embedding and a generalized correlator detector. EURASIP Journal on Applied Signal Processing 2004,2004(8):1088-1106. 10.1155/S1110865704402029
Ng TM, Garg HK: Maximum-likelihood detection in DWT domain image watermarking using Laplacian modeling. IEEE Signal Processing Letters 2005,12(4):285-288.
Do MN, Vetterli M: Wavelet-based texture retrieval using generalized Gaussian density and Kullback-Leibler distance. IEEE Transactions on Image Processing 2002,11(2):146-158. 10.1109/83.982822
Cohen A, Daubechies I, Feauveau J-C: Biorthogonal bases of compactly supported wavelets. Communications on Pure and Applied Mathematics 1992,45(5):485-560. 10.1002/cpa.3160450502
Hopper T, Brislawn C, Bradley J: Wsq grey-scale fingerprint image compression specification, version 2.0. Criminal Justice Information Services, Federal Bureau of Investigation, Washington, DC, USA; February 1993.
WSQ viewer (version 2.7) http://www.cognaxon.com/index.php?page=wsqview
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License ( https://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Zebbiche, K., Khelifi, F. & Bouridane, A. An Efficient Watermarking Technique for the Protection of Fingerprint Images. EURASIP J. on Info. Security 2008, 918601 (2008). https://doi.org/10.1155/2008/918601
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1155/2008/918601




 is partitioned into
is partitioned into 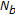 nonoverlapping sets
nonoverlapping sets  . In the following we denote by
. In the following we denote by 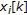 the coefficients belonging to the set
the coefficients belonging to the set 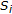 , where
, where  for
for  and
and  .
.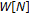 is divided into
is divided into  nonoverlapping chunks
nonoverlapping chunks 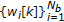 , where
, where 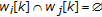 for
for 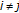 and
and 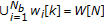 , so that each chunk
, so that each chunk  is associated to one block
is associated to one block 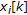 and both are used to carry one information bit
and both are used to carry one information bit 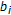 .
.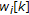 is multiplied by +1 or -1 according to its associated information bit
is multiplied by +1 or -1 according to its associated information bit  . The result of this multiplication is an amplitude-modulated watermark
. The result of this multiplication is an amplitude-modulated watermark 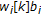 .
.
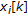 and
and 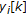 represent the set of the original coefficients and the associated watermarked coefficients belonging to the set
represent the set of the original coefficients and the associated watermarked coefficients belonging to the set 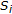 , respectively.
, respectively. 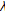 is a gain factor used to control the strength of the watermark by amplifying or attenuating the watermark effect on each DCT coefficient, so that the watermark energy is maximized while the alterations suffered by the image are kept invisible.
is a gain factor used to control the strength of the watermark by amplifying or attenuating the watermark effect on each DCT coefficient, so that the watermark energy is maximized while the alterations suffered by the image are kept invisible.




 using the conventional technique.
using the conventional technique.
 using the conventional technique.
using the conventional technique.
 using the conventional technique.
using the conventional technique.





